VULNERABILITY RESEARCH
What is a zero-day vulnerability?
A zero-day is a yet unknown and undisclosed vulnerability. As long as it remains unknown, the vendor cannot release a patch and common defense mechanisms are not able to detect any attack exploiting it.
«Knowledge of new vulnerabilities gives cyber criminals a free pass to attack any target of their choosing, while remaining undetected. […] A typical zero-day attack lasts 312 days on average»
- L. Bilge, T. Dumitras, "Before We Knew It: An Empirical Study of Zero-Day Attacks In The Real World”
♙ the good
the bad ♟
Big corps, such as Facebook, often use zero-day vulnerabilities in large-scale red team exercises. Facebook admitted that approach has greatly improved the CERT ability to respond to real attacks and face complex threats.
The well known malicious computer worm Stuxnet, capable to sabotage nuclear power plants, exploited many high-value zero-day vulnerabilities to spread on Windows machines and compromise PLC and SCADA systems.
Zero-day flaws support government and law enforcement agencies in lawful operations, aimed at fighting and tracing criminals and terrorists. In 2016, the FBI bought and used a zero-day vulnerability to access the San Bernardino iPhone.
In 2013, Facebook developers laptops were infected by a malware, injected via a web-hosted exploit that leveraged a Java zero-day vulnerability. The laptops were fully-patched and running up-to-date anti-virus softwares.
Security solutions vendors continuously update their products with zero-day related information, in order to increase detection and protection capabilities. As an instance, Beyond Security integrates significant zero-day intelligence into their popular AVDS vulnerability assessment solution to sharpen its effectiveness.
According to Symantec, in 2015 a new zero-day vulnerability was discovered each week, not counting those remained undisclosed. Some of them were leveraged to perform attacks and distribute new malwares. As an example, the notorious Locky ransomware was pushed via a zero-day flaw in Adobe Flash Player.
What are TRUEL IT capabilities and how does it operate?
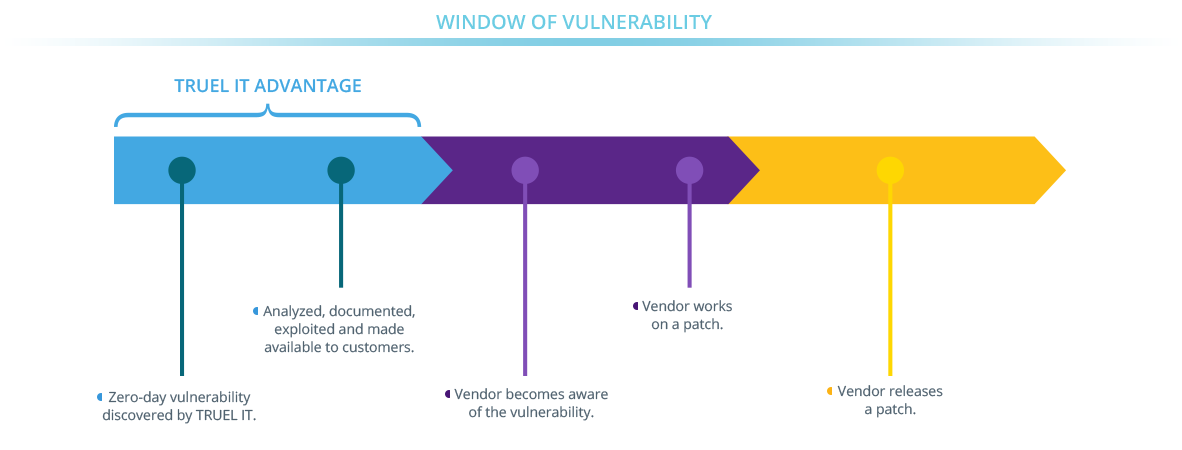
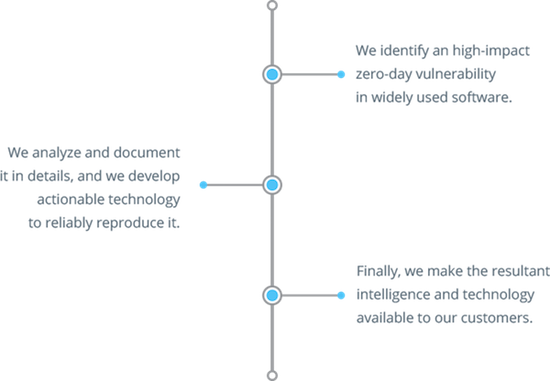
TRUEL IT is highly specialized in critical zero-day vulnerability discovery and exploitation. By providing such security intelligence, we enable our customers to integrate it into security solutions, enforce proactive protection and devise new mitigation and prevention techniques.
We ensure that all our items are
- Delivered with detailed technical documentation and proof-of-concept exploits;
- Proven to be exploitable: we do not deal with theoretical vulnerabilities and we always provide actionable technology;
- Researched in-house by our internal research team, through custom methodologies and ad-hoc techniques;
- Available with different licensing plans such as, for example, exclusivity or redistribution rights;
What do the provided intelligence and technology actually consist of?
Contact us to have a comprehensive overview of the information and resources included in our deliverables.
Vulnerabilities and exploits may have a dual use. How does TRUEL IT relate with this?
TRUEL IT operates in full compliance with applicable laws. In addition, TRUEL IT selects its customers according to internal criteria of eligibility and integrity.
Is TRUEL IT available for on-demand research projects, for example, in the form of private engagement?
Yes. We sometimes receive requests that do not fall within our research perimeter: we are always interested in new challenges.